아큐네틱스 웹 취약성 점검도구 - Review
A REAL WORLD REVIEW
MSI::Labs
2006년 5월
아큐네틱스 웹 취약점 점검 도구는?
아큐네틱스 웹 취약점 점검 도구는 웹 애플리케이션에서 보안 허점 – 이는 공격자가 시스템과 데이터로의 불법적인 접근을 획득하기 위해 악용될 수 있습니다 - 을 찾아내기 위해 만들어진 도구입니다. 이는 SQL injection, Cross Site Scripting과 암호 취약점 등을 포함한 다중의 취약점들을 찾아줍니다.
본
제품은
웹과
애플리케이션
취약점을
점검을
실행하기
위해
이용될
수
있고, 확인된
문제점에
대한
모의침투
검사를
실행하기
위해
이용
될
수
있습니다. 각
취약점에
제공되는
완화제안들(mitigation suggestions)은
검사된
웹
서버
또는
애플리케이션의
보안성을
향상시키는데
이용
될
수
있습니다.
본
리뷰는
MicroSolved, Inc는 Real World 테스트에
아큐네틱스를
이용하였습니다. 실제
취약점
평가와
침투
테스트
동안
나타낸
내용으로
검사하였습니다.
본
데스트는
수많은
침투테스트
경험과
광범위한
상용
및
오픈
소스
웹/애플리케이션
점검
도구들에
대한
지식을
겸비한
전문
패널에
의해
실행되었습니다. 테스트
동안, 다수의
웹
사이트가
평가되었습니다. 본
이들
웹
사이트와
본
침투테스트에서
점검항목은
본
리뷰
중
입력값처럼
이용됩니다. 아큐네틱스
웹
취약점
분석도구의
각
기능은 1-5의
척도로
표시되었고, 5가
가장
좋은
점수가
됩니다.
설치
및
업데이트
구조
설치는
바로
진행됩니다. 전형적인
윈도우
설치
절차가
실행
가능하도록
제공됩니다. 설치를
위해
필요한
유일한
입력값은
발급된
라이센스입니다. 본
프로그램은
업데이트
구조를
내장하여
제공하고
있습니다. 아큐네틱스는
프로그램을
재
시작하지
않고도
업데이트된
내용을
적용하는
것이
가능합니다. 아큐네틱스는
시작시
업데이트를
확인하거나
업데이트
기능을
매뉴얼로
이용할
때만
확인할
수
있도록
설정할
수
있는
선택사항을
가지고
있습니다.
점검
도구
설명
점검도구의
인터페이스는
기능에
의해
수행업무가
배분됩니다. 데이터가
도구간에
공유, 복사
그리고
붙여지는
동안, 해당
인터페이스는
웹
애플리케이션
평가
실행과
함께
연계되어
수행
업무를
처리하는
논리적이고
효과적인
방법을
생성합니다. 각각의
고유한
도구와
기능은
다음과
같습니다.
웹
스캐너(Web Scanner): 
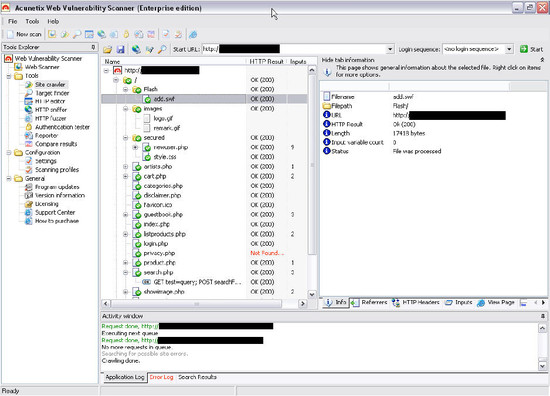
Rating: 4.5
점검 대상 찾기 도구(Target Finder):
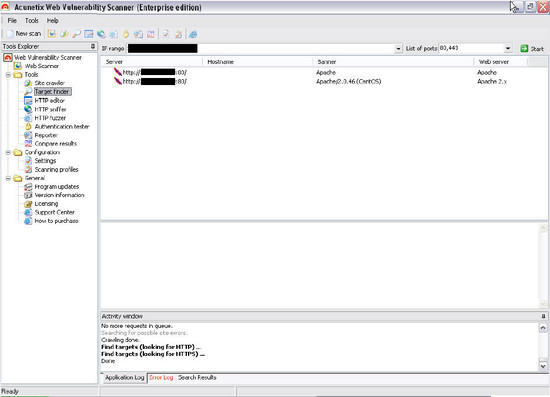
대상 찾기 도구는 주어진 주소의 범위에서 웹 사이트를 찾을 수 있게 설계된 간단한 포트 스캐너입니다. 주소의 범위는 한정되지 않았고, 표준포트를 사용하지 않는 웹 사이트를 발견할 수 있게 원하는 포트를 찾아볼 수 있도록 특정할 수 있습니다. 또한 사용중인 웹 서버의 종류를 판별하기 위한 시도도 합니다.
Rating: 4
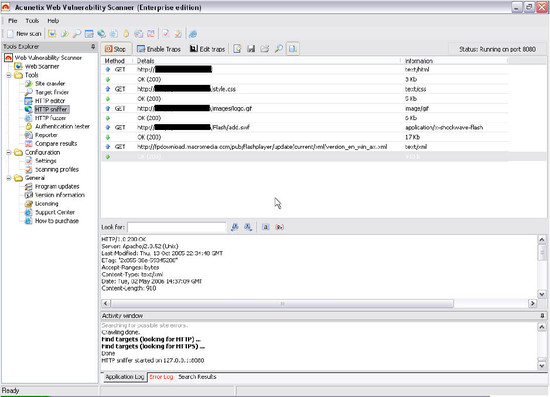
HTTP 퓨져(HTTP Fuzzer):
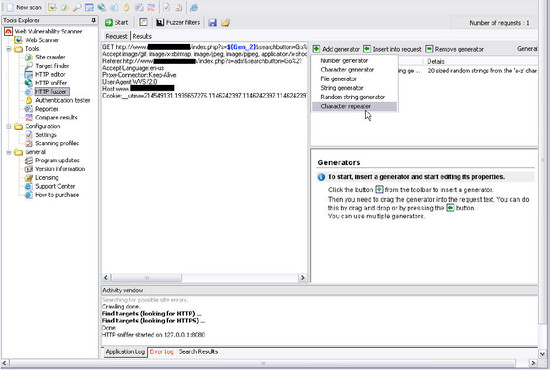
Rating: 4
인증 검사 도구(Authentication Tester):
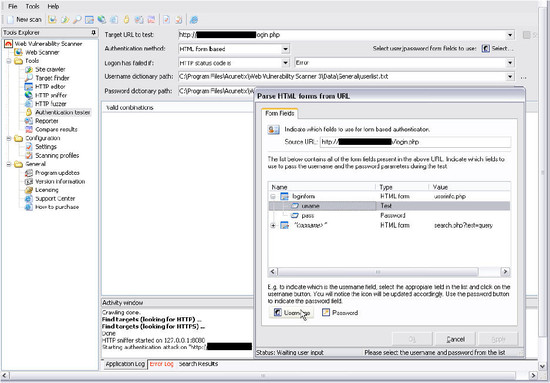
Rating: 4
보고서
기능(Reporting Capabilities)
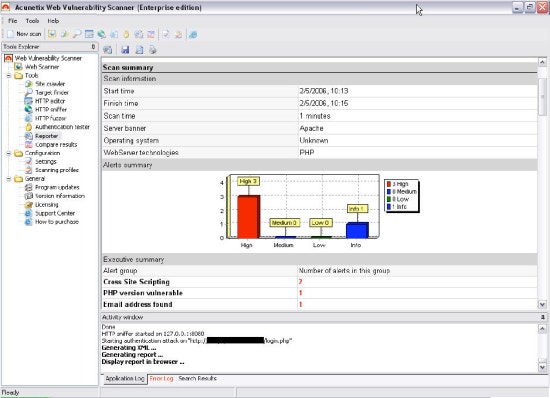
보고서는 충분할 만큼 제공됩니다. 본 보고서는 잘 정리되어 있고, 쉽게 읽을 수 있으며, 중요하지 않은 취약점들에 대해 부적당한 등급을 주지 않았습니다. 전반적인 취약점은 다른 많은 점검도구 중에서도 불합리한 공포나 행동을 조장하지 않을 만큼 일반적인 사례처럼 보여집니다. 하지만, 보고서는 HTML 형태의 문서로만 저장될 수 있습니다. Acunetix는 XML과 같은 다른 형태로 바꿔줄 수 있는 직접적인 방법을 가지고 있지 않고, 입력된 데이터를 다른 보다 확장된 보고서 도구로 전해줄 방법도 없습니다. 기본적으로, 아큐네틱스는 모든 데이터를 MS Access 데이터베이스에 저장할 수 있습니다. 혹시 마이크로소프트 액세스를 이용할 수 있다면, 수많은 다른 형태로 전해줄 수 있습니다. 보고서는 간결하지만, HTML 형태가 아닌 데이터로 전할 직접적인 방법이 없어, 사용자가 필요로 하는 보고서에 의해 결정되는 이들에게는 문제가 될 수 도 있습니다.
전반적인
제품
평점
상당한
기능, 사용
편의성
그리고
빠른
처리능력으로, 아큐네틱스에
별 4개의
전반적인
평점을
주었습니다.
장점:
+ 빠른
점검
기능
+ 자체제작
에러
페이지들에
대한
특정
기능
+ 하나의
애플리케이션에
조합된
많은
도구들
+ 높은
취약점
탐지율
+ 중요하지
않은
취약점에
대한
적절한
위협
분류
단점:
- 다양하게
제공
되지
못하는
보고기능
- 대상
점검
도구에
버그가
있어
보임
- 몇몇
인터페이스
트윅을
사용할
수
있음
요약
아큐네틱스는
웹
사이트의
취약점을
완벽하게
찾아볼
수
있도록
제공되는
완벽한
도구들의
모음을
포함한
하나의
애플리케이션을
만들기
위해
노력했습니다. 전반적으로, 아큐네틱스는
이러한
목표를
이루었지만, 다이아몬드처럼
빛나는
완전한
패키지로
만들기
위해
제품의
중요하지
않은
기능에
어느
정도
노력을
가해
그
빛을
더하게
할
수
있었습니다.
앞으로
개선을
위한
제안
아큐네틱스는
이미
강력한
도구이자
제품이지만, 몇몇
중요하지
않은
부가적인
기능을
통해
이미
훌륭한
도구로
향상할
수
있었습니다. 본
리뷰를
통해
몇
가지
포함돼야
하거나
바뀌어야
할
소소한
부분을
발견했습니다. 사용자
인터페이스가
친
사용자적이고, 이용에
편리함에도
불구하고
사용자
인터페이스는
조금
손볼
필요가
있으며, 특별히
fuzzer의
경우가
그렇습니다. 인증
검사도구의
경우, HTML 브루트
포싱을
하는
동안
사용자
이름
없이
암호만을
지정할
수
없었습니다. 암호
입력만이
요구되는
몇몇
“관리자” 웹
페이지에
실행해
보았습니다만, 해당
페이지를
브루트
포스
할
방법을
찾아내지
못했습니다. 게다가, 타임아웃
기간과
다중
처리를
바꾸는
방법
역시
환영
받을
수
있는
추가사항입니다. 이를
통해
점검
속도의
증가가
제공될
것입니다. 수집기에서, 수집되는
링크의
depth를
제한하기
위한
것은
유리할
수
있습니다. 이는
수집기가
무한루프에
빠져
발생하는
문제에
대한
대안을
제공할
수
있을
것
입니다.
Acunetix는 (from www.acunetix.com)
Securing a company's web applications is today's most overlooked
aspect of securing the enterprise. Web applicationhacking is on the rise with as
many as 75% of cyber attacks done at web application level or via the web. Most
corpo-rations have secured their data at the network level, but have overlooked
the crucial step of checking whether theirweb applications are vulnerable to
attack. Web applications, which often have a direct line into the company's most
valuable data assets, are online 24/7, completely unprotected by a firewall and
therefore easy prey for attackers.
Acunetix was founded with this threat in mind. They realized the only
way to combat web site hacking was to de-velop an automated tool that could help
companies scan their web applications for vulnerabilities. In July 2005,
Acu-netix Web Vulnerability Scanner was released -a tool that crawls the website
for vulnerabilities to SQL injection, cross-site scripting and other web attacks
before hackers do.
The Acunetix development team consists of highly experienced security
developers who have each spent years de-veloping network security scanning
software prior to starting development on Acunetix WVS. The managementteam is
backed by years of experience in marketing and selling security software.
Acunetix is a privately held company with its offices in the
MicroSolved, Inc.은
MicroSolved, Inc. was founded in 1992 by L. Brent Huston. MSI was
created to provide solutions that empower organizations to mitigate risks and
create privacy while maintaining the practice of doing business in the online
world. The projects MSI engages in range from managed security services to
unique solutions crafted to answer complex security problems. Our work includes
protecting the largest government and commercial networks in the world.
MSI’s public work includes engagements on the Federal, State, and
local level. Our work with the federal govern-ment includes protecting some of
our nation’s most sensitive networks, working to secure some of the largest
HIPAAnetworking concerns, and working with federal auditing agencies to help
them implement an auditing process thateffects real world security. MSI has
received accolades for its work for the
MSI’s work in the commercial sector includes a wide variety of
vertical markets. MSI enjoys long-term relationshipswith some of the world’s
largest financial and telecom providers. Our work with various regulations
including GLBAand HIPAA has made us an obvious choice for financial and
healthcare organizations of all sizes. In the commercialsector our work ranges
from the fortune 50 to working within the budget needs of small businesses.
What we’re most proud of, however, is our work for the community. MSI
has sponsored and contributed to variousopen source initiatives. We’ve
contributed intellectual capital pro bono to various working groups and security
orga-nizations.
Our goal with each engagement is to preach security philosophy, transfer knowledge to client stakeholders, and to build a long-term relationship steeped in trust, understanding, and open communication.